Single Sign-On (SSO) with Microsoft Entra: Best Practices and Step-by-Step Implementation Guide
In today’s digital landscape, secure and streamlined access to applications is crucial for business efficiency and data protection. Single Sign-On (SSO) is a key feature of modern identity and access management (IAM) systems that significantly enhances security and user experience. With Microsoft Entra, organizations can leverage SSO to provide seamless access to both cloud and on-premises applications, allowing users to authenticate once and access multiple resources without re-entering their credentials.
In this SEO-optimized blog, we’ll explore the concept of SSO in Microsoft Entra, highlight the best practices for its implementation, and provide a detailed step-by-step guide to enabling SSO in your organization.
What is Single Sign-On (SSO) in Microsoft Entra?
Single Sign-On (SSO) in Microsoft Entra allows users to authenticate once with their credentials and gain access to multiple applications without needing to re-enter their information. Microsoft Entra integrates with various SaaS and custom applications, providing secure, streamlined access and reducing the need for managing multiple sets of credentials.
Key Benefits of SSO in Microsoft Entra:
- Enhanced Security: Reduces the attack surface by minimizing the number of credentials that need to be managed and remembered, lowering the risk of phishing and credential theft.
- Improved User Experience: Enables users to access all applications with a single login, reducing login fatigue and increasing productivity.
- Simplified IT Management: Centralizes authentication and access management, making it easier for IT teams to enforce security policies and maintain compliance.
Best Practices for Implementing SSO with Microsoft Entra
- Adopt a Federated Identity Model:
- Use Microsoft Entra ID (Azure Active Directory) to establish a federated identity model. This ensures users authenticate through a single trusted identity provider (IdP), enhancing security and simplifying access management.
- Enable Multi-Factor Authentication (MFA):
- Combine SSO with Multi-Factor Authentication (MFA) to add an extra layer of security. This ensures that even if a user’s credentials are compromised, an additional factor (like a biometric or one-time passcode) is needed to gain access.
- Implement Conditional Access Policies:
- Utilize Conditional Access in Microsoft Entra to enforce dynamic security policies based on user behavior, device status, location, and risk level. For example, require MFA for access attempts from untrusted networks.
- Regularly Review and Monitor Access:
- Regularly audit user access and monitor sign-in activity for any unusual behavior. Microsoft Entra offers built-in monitoring tools and reporting features to identify anomalies or potential security threats.
- Automate User Lifecycle Management:
- Integrate Microsoft Entra with HR systems to automate user provisioning and deprovisioning, ensuring that access is granted or revoked as needed, reducing the risk of unauthorized access.
- Educate Users:
- Provide regular training sessions to educate users on the benefits and security implications of SSO, emphasizing the importance of safeguarding their credentials.
Step-by-Step Procedure to Implement SSO with Microsoft Entra
Step 1: Prepare Your Environment
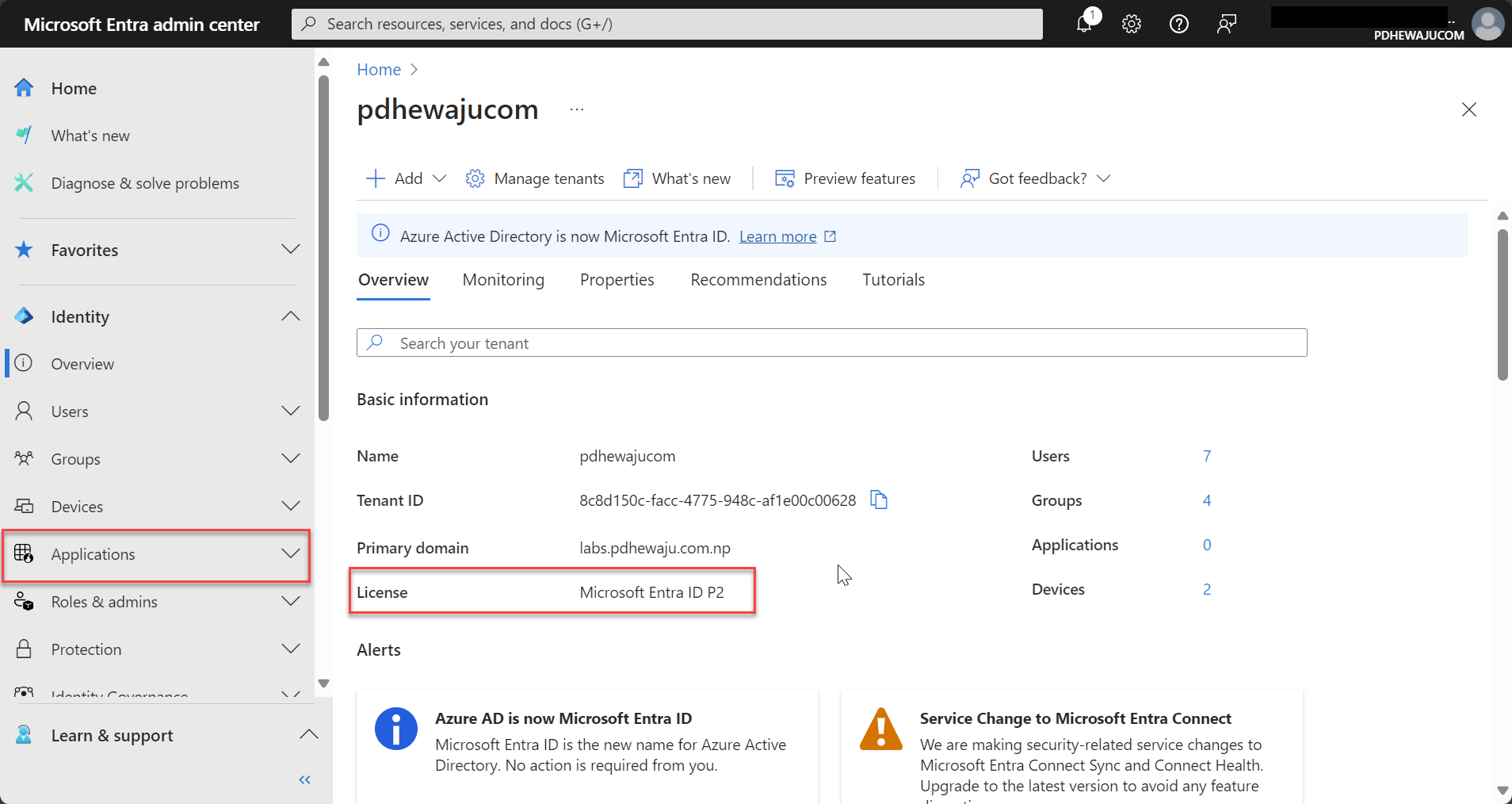
- Verify Licensing Requirements:
- Ensure you have the appropriate Microsoft Entra license (such as Microsoft Entra ID P1 or P2), which includes SSO capabilities.
- Assess Your Application Landscape:
- Identify the applications to be integrated with SSO. Microsoft Entra supports various apps, including SaaS, on-premises, and custom applications.
- Set Up Your Microsoft Entra Tenant:
- Set up your Microsoft Entra tenant and connect it to your on-premises Active Directory using Azure AD Connect.
Step 2: Configure SSO for Your Applications
- Access the Microsoft Entra Admin Center:
- Go to the Microsoft Entra admin center and select “Enterprise applications” from the left menu.
- Add an application:
- Click “+ New application” and choose the application you want to configure for SSO from the gallery or add a custom app.
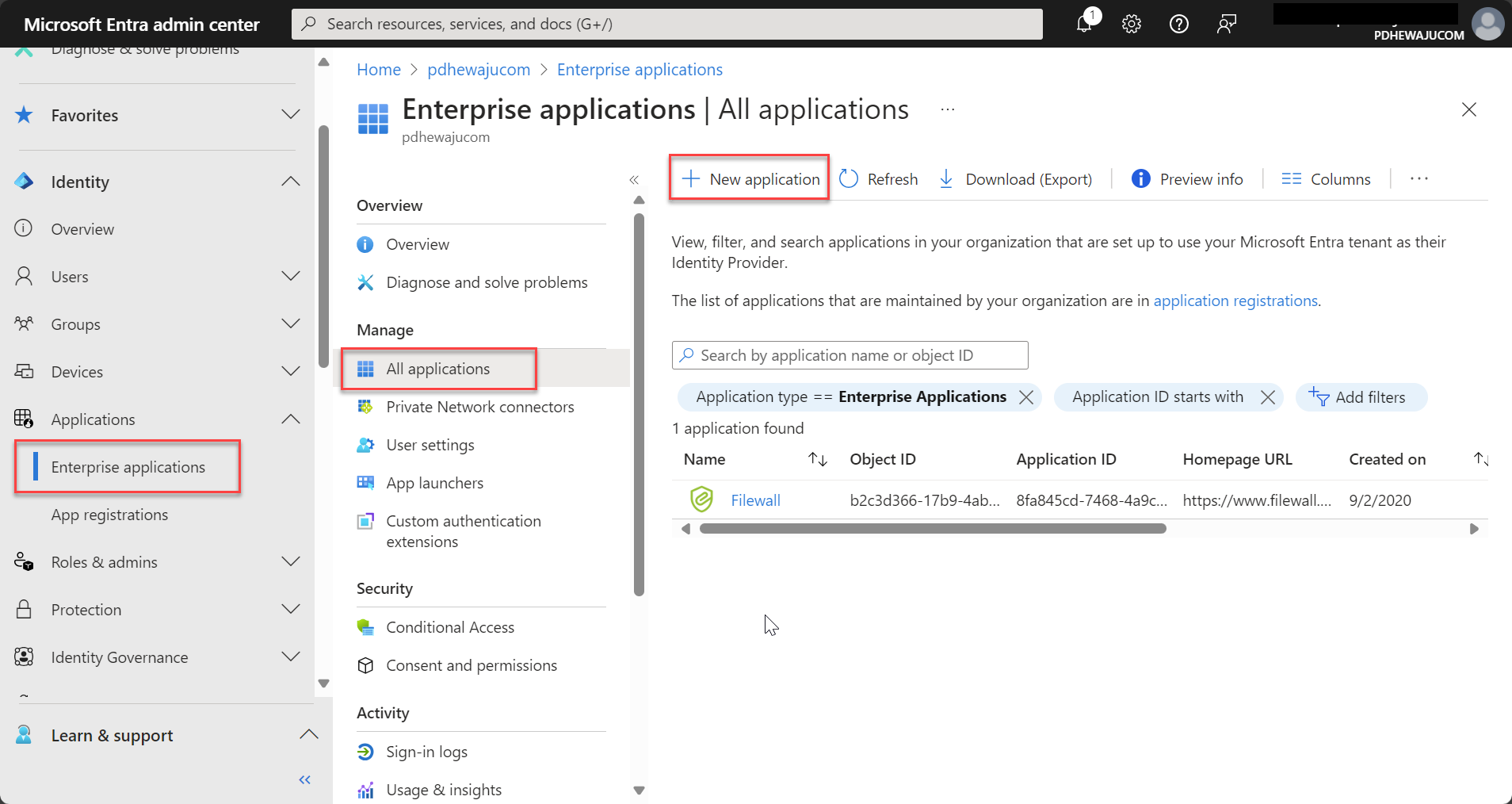
You can either choose an available configuration from gallery or can create a custom one.
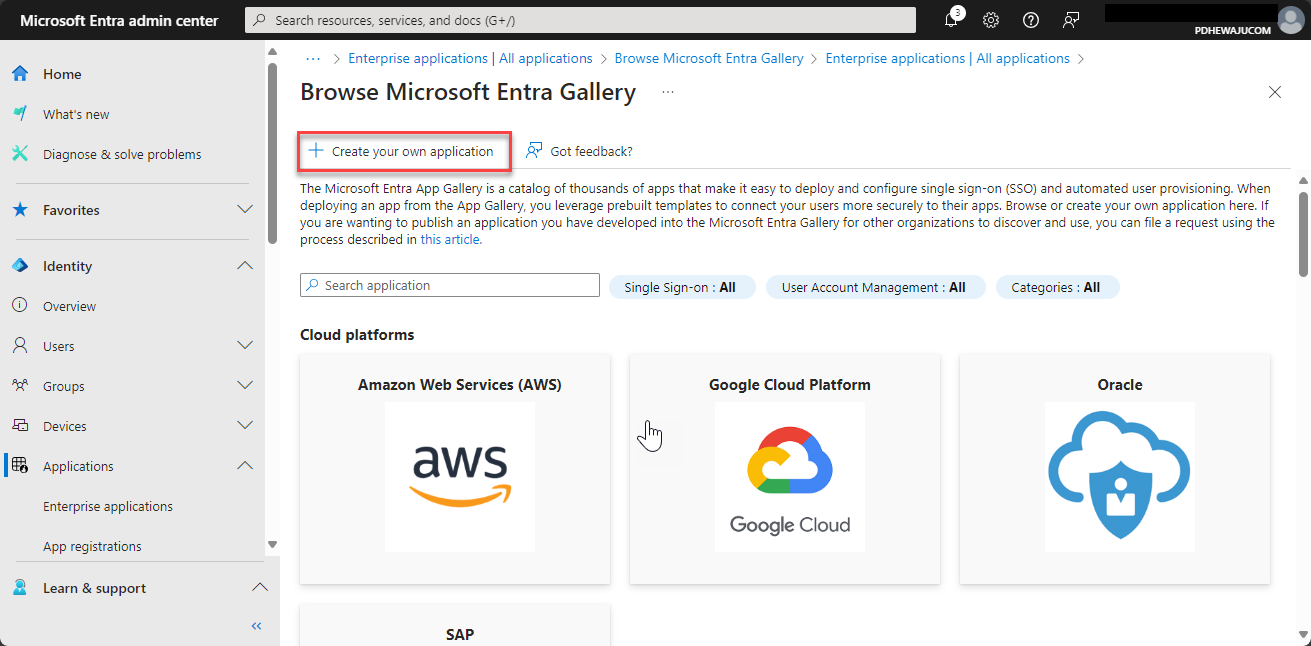
Here I have created a custom one to integrate any other application from gallery.
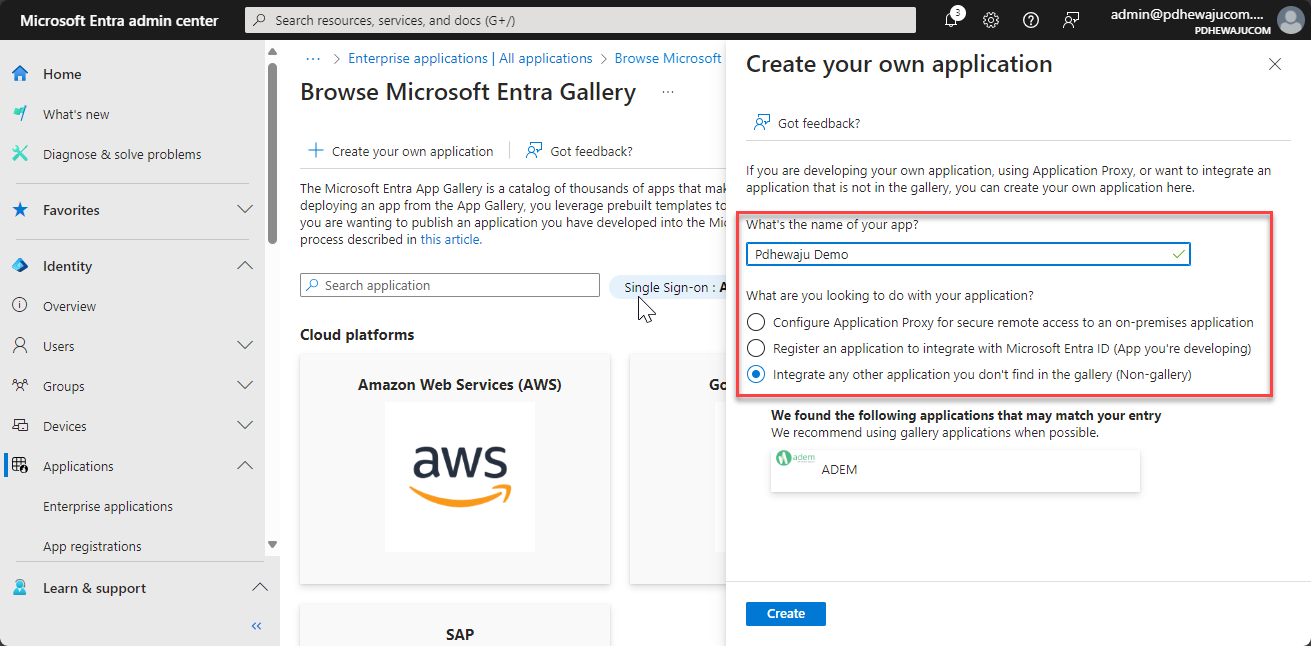
- Select the SSO Method:
- Choose the SSO method that fits your application:
- SAML-Based SSO: Ideal for applications supporting SAML 2.0, allowing identity assertion between the identity provider and service provider.
- Password-Based SSO: Securely stores user credentials in Microsoft Entra and uses them to authenticate on behalf of the user, suitable for applications that do not natively support SSO.
- OpenID Connect (OIDC) or OAuth-Based SSO: For modern applications using OIDC or OAuth for authentication.
For my application it was SAML, so I choose SAML method.
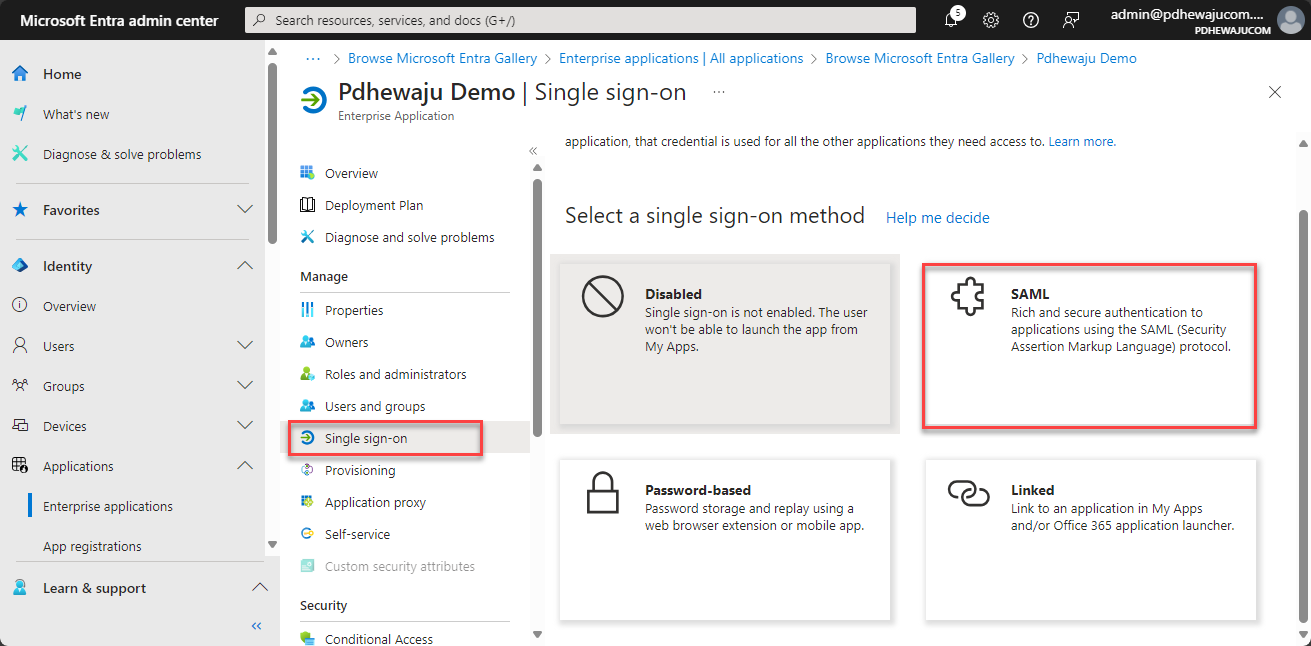
- Configure SSO Settings:
- Follow specific configuration steps for your chosen SSO method. For SAML-based SSO, upload the SAML metadata file, map user attributes, and define the application’s sign-on URL and identifier.
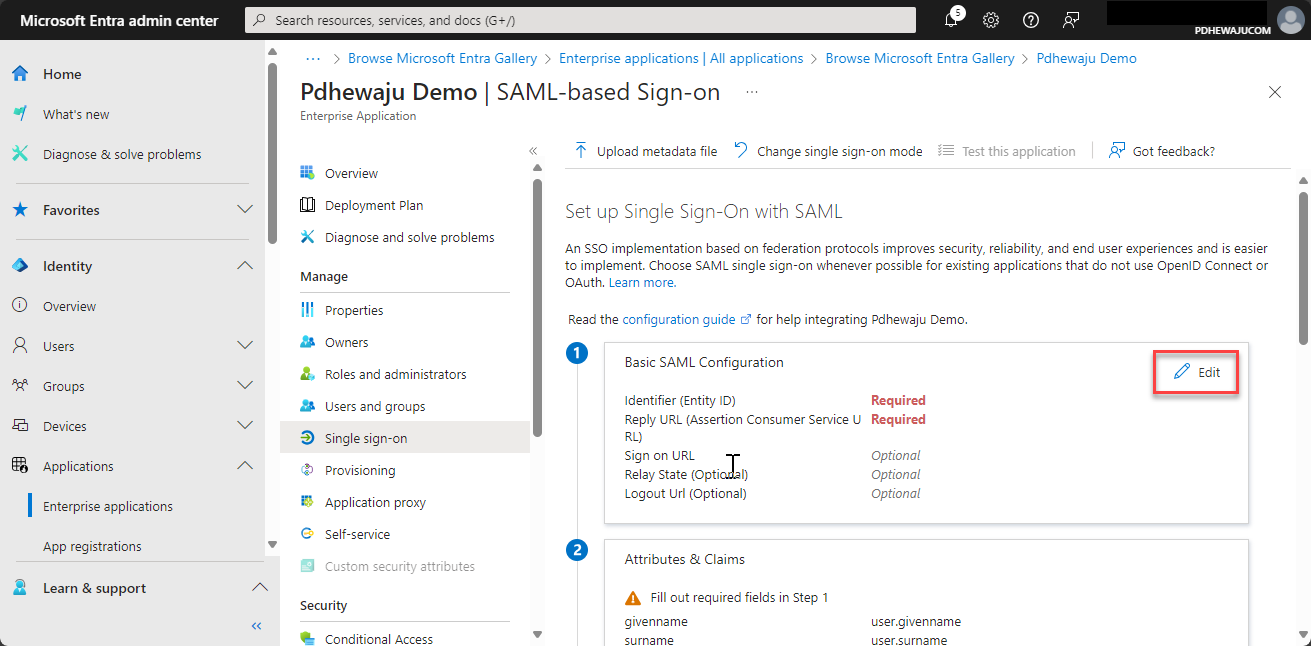
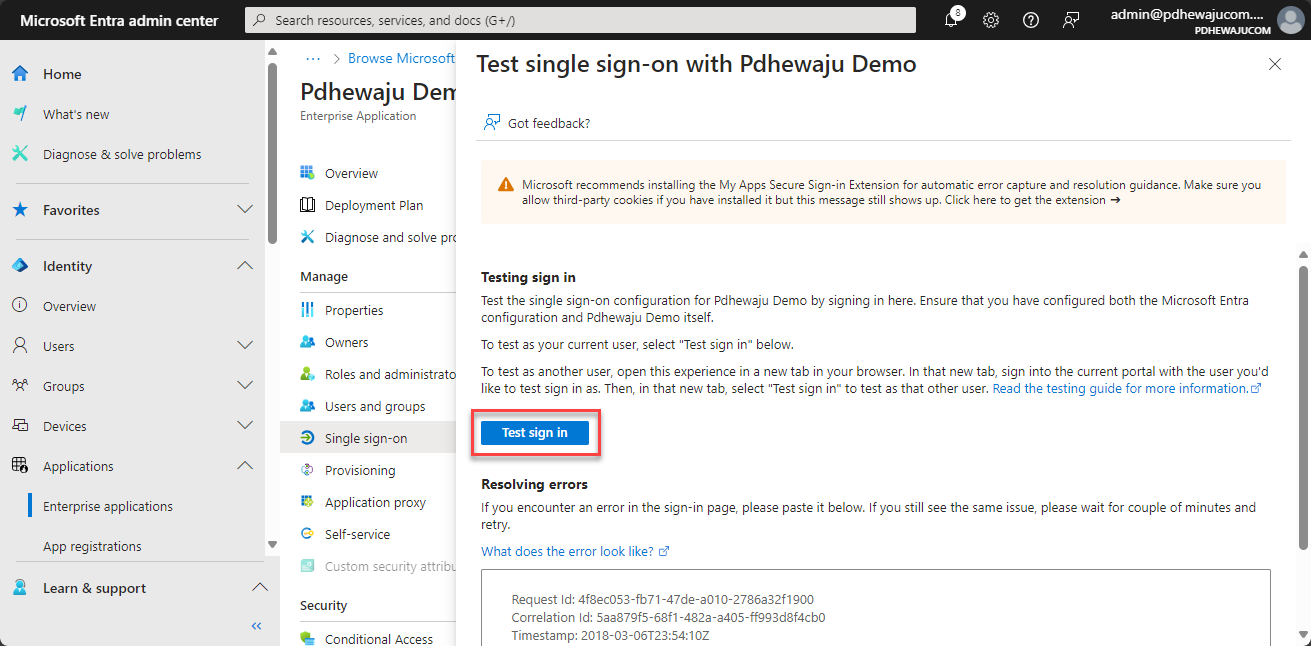
- Test the SSO Configuration:
- Use the “Test single sign-on” feature in the Microsoft Entra admin center to verify that SSO is configured correctly, and users can access the application without re-authenticating.
Step 3: Roll Out SSO to Users
- Inform and Train Users:
- Communicate the new SSO experience to your users and provide training on how to use it.
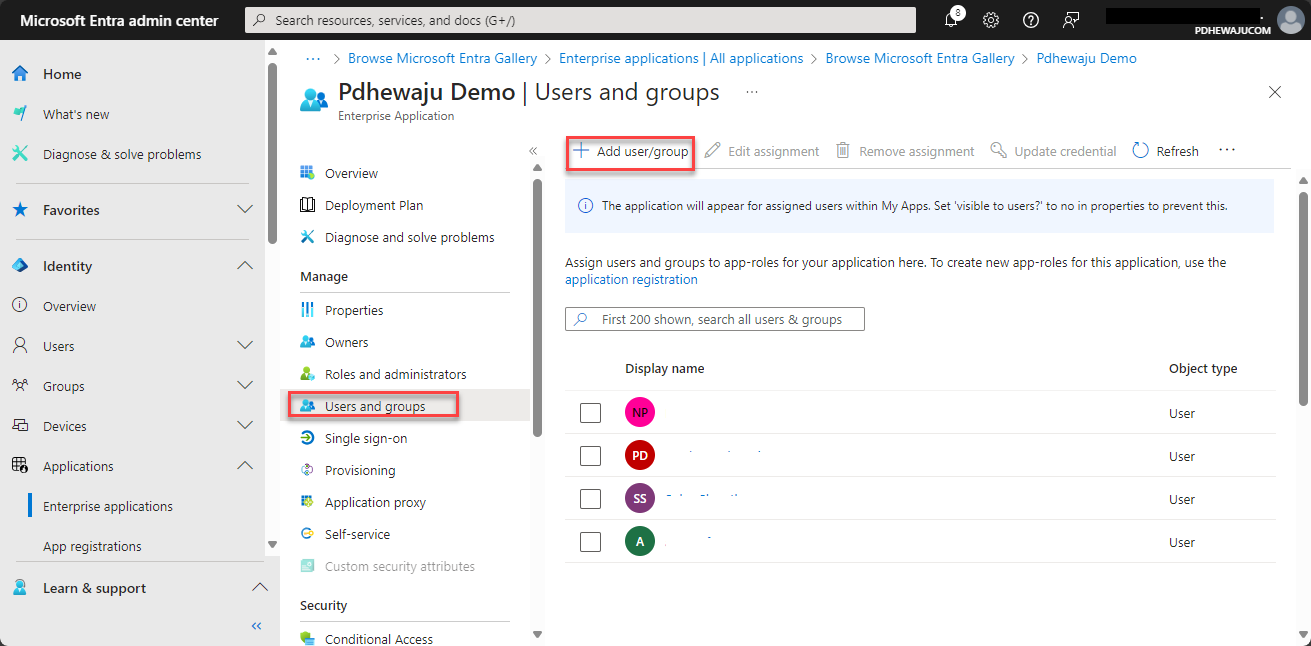
- Enable for Selected Users or Groups:
- Roll out SSO to a small group of users first to test and gather feedback. Once confirmed, expand the rollout to the entire organization.
Step 4: Monitor and Optimize
- Monitor User Activity:
- Utilize Microsoft Entra’s audit logs and sign-in reports to monitor user activity, identify potential security risks, and ensure compliance.
- Adjust Conditional Access Policies:
- Refine your Conditional Access policies based on user behavior and emerging security threats.
- Collect Feedback and Iterate:
- Regularly gather user feedback to identify any issues or areas for improvement and make necessary adjustments to optimize the SSO experience.
Conclusion
Implementing Single Sign-On (SSO) with Microsoft Entra enhances your organization’s security posture and simplifies access management. By following best practices and a structured implementation procedure, you can ensure a secure, seamless user experience across all applications. Additionally, leveraging features like MFA, Conditional Access, and regular monitoring will further strengthen your identity protection strategy.
Ready to implement SSO? Start exploring Microsoft Entra’s capabilities today and secure your organization’s digital identities effectively.

