[How to]Configure Azure RMS for Exchange Online /O365
On my previous blog, I have shared my knowledge regarding the security of the Organization with DLP on Document Fingerprints. As all of know how crucial email has been these days, even for any official approval or submission or information circulation we use email. If such critical information on email gets leaked, it might burn down all the organization. Hence, we need to have a proper security with emails. Here today, on this blog we will be configuring Azure RMS (Right Management Service) for Exchange Online / O365. The questions may be why do we need RMS for Exchange Online / O365 or how will RMS secure email on Exchange Online / O365. RMS is the functionality that allows user to protect sensitive emails by not allowing recipient to Forward, copy, print or take snapshot of that emails. Azure RMS can be configured for office products and On-Premises Exchange server too, wait until the blog comes for it. J
Before Starting this blog, let me inform you to use this security feature you need to have Azure Information Protection Plan1 at least. Below is the snap with the information of Azure Information Protection Plan 1. For the blogging purpose, I am in the trial function. Even though you are on trial, you will have full functionalities with limit of 30 days.
To have a trial license, it is quite easy. You just go to your subscription menu, Click on Add Subscriptions and select ‘Azure Information Protection Plan 1‘ as on the below snap.
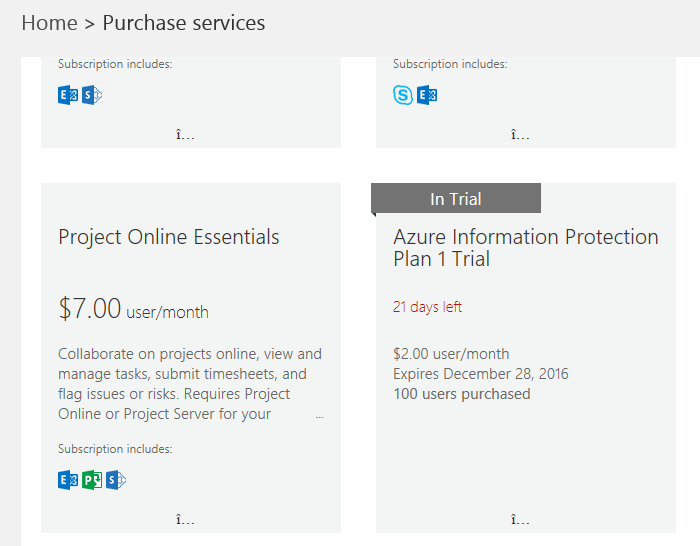
Once you subscribe the plan, you will have something like below on the Subscription page. This is the confirmation that you have subscribed the ‘Azure Information Protection Plan‘
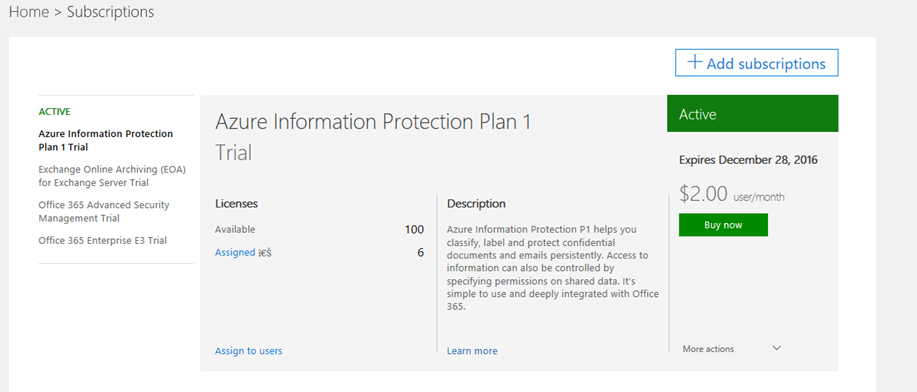
Now after the subscription, we need to assign the license to the user’s whom we would like to provide these kinds of the features.
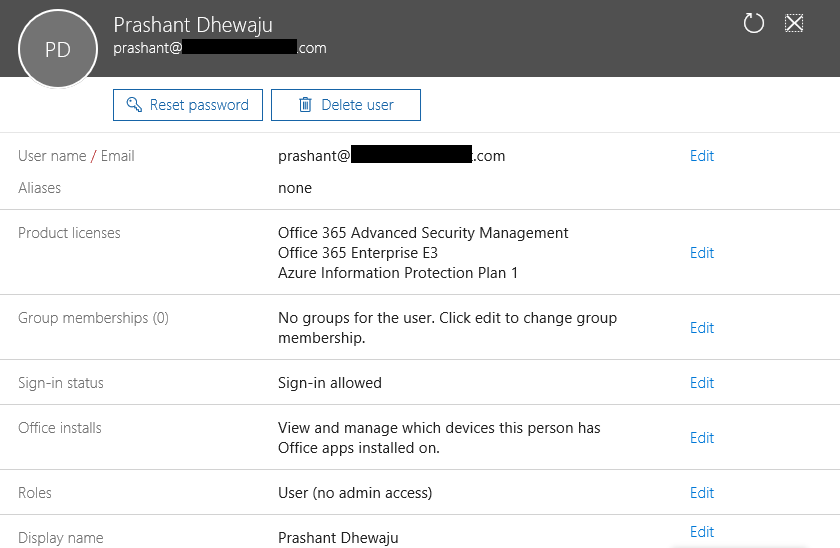
Once license is assigned to the user, it’s time for few configuration needs to make change to activate RMS Features for the users. To configure the RMS, first need to have Azure PowerShell tool and install on your machine. Which will help us to connect Exchange Online /O365 using PS cmdlet. To download Azure PowerShell tool, Click here .
After the installation of the of Azure PowerShell, Open it with Administrative privilege and run the below command to
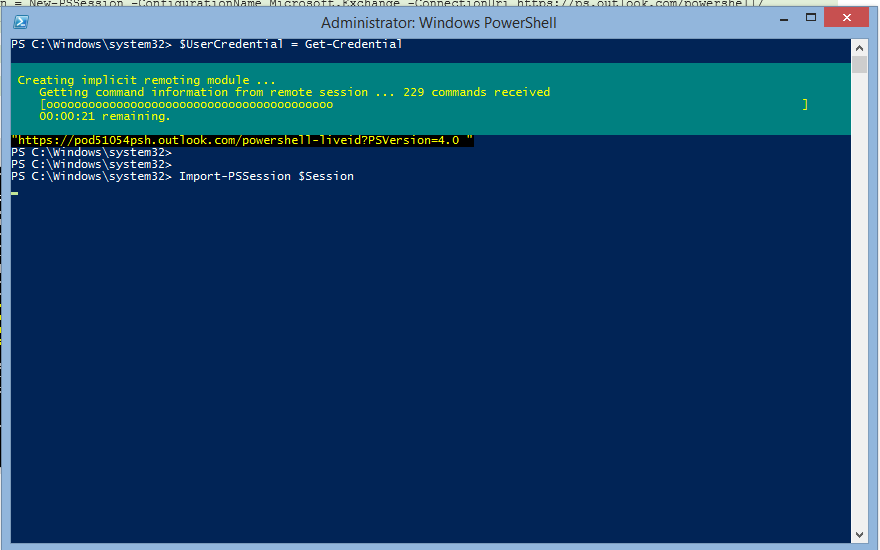
$UserCredential = Get-Credential
This command will prompt to enter you, your credentials of Exchange Online/ O365 administrative privilege.
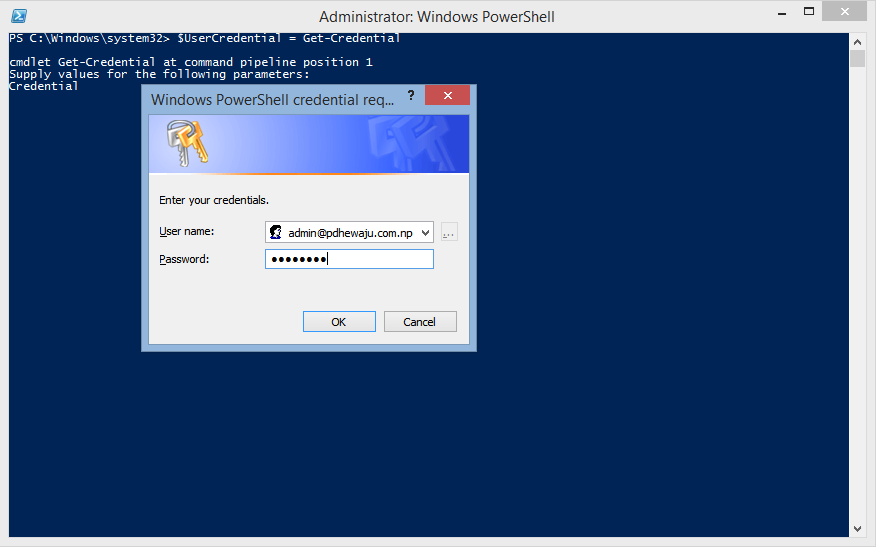
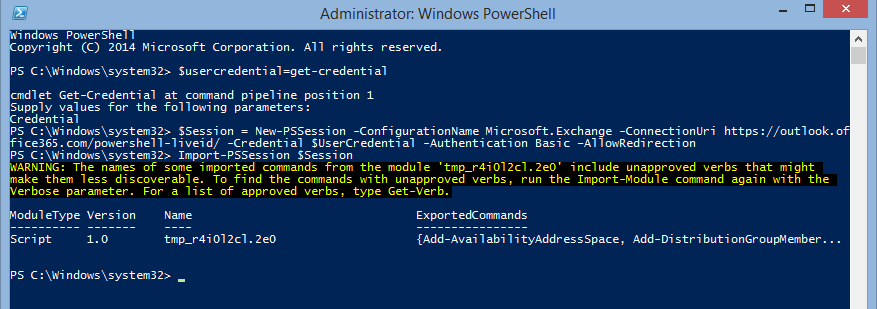
After providing the credentials, run below command to access the PS session of your Exchange Online/ O365
$Session = New-PSSession -ConfigurationName Microsoft.Exchange -ConnectionUri https://ps.outlook.com/powershell/ -Credential $UserCredential -Authentication Basic –AllowRedirection
Import-PSSession $Session
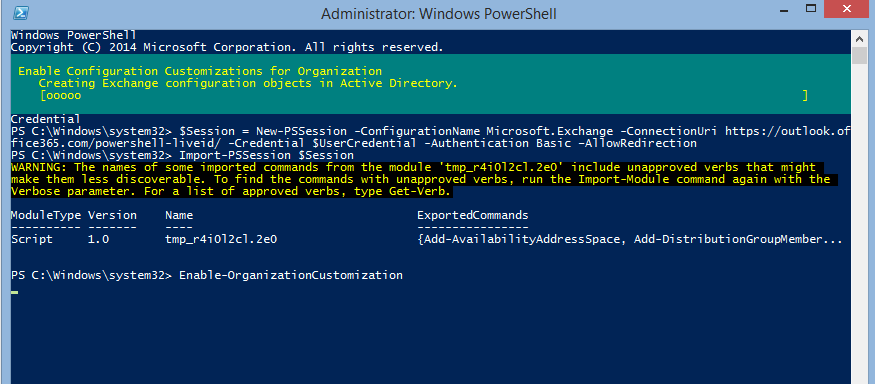
After Session of your Exchange online / O365 is imported, you need to Enable the customization of your Organization. Which can be done by below cmdlet.
Enable-OrganizationCustomization
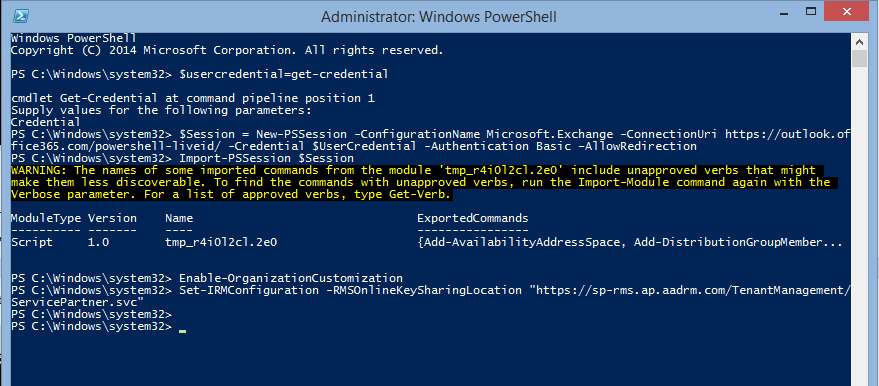
During the configuration, we need to be careful with our next cmdlet. This cmdlet will configure the RMS for our emails, and should be applied as per the region. Below is the cmdlet that I have used on Asia region.
Set-IRMConfiguration -RMSOnlineKeySharingLocation "https://sp-rms.ap.aadrm.com/TenantManagement/ServicePartner.svc"
If I have to configure the RMS for European Union, I have to re-write this cmdlet as of below:
Set-IRMConfiguration -RMSOnlineKeySharingLocation "https://sp-rms.eu.aadrm.com/TenantManagement/ServicePartner.svc"
This is the table that can help you to identify the RMS key Sharing location according to your organization location.
| Location | RMS key sharing location |
| North America | https://sp-rms.na.aadrm.com/TenantManagement/ServicePartner.svc |
| European Union | https://sp-rms.eu.aadrm.com/TenantManagement/ServicePartner.svc |
| Asia | https://sp-rms.ap.aadrm.com/TenantManagement/ServicePartner.svc |
| South America | https://sp-rms.sa.aadrm.com/TenantManagement/ServicePartner.svc |
| Office 365 for Government (Government Community Cloud) | https://sp-rms.govus.aadrm.com/TenantManagement/ServicePartner.svc (1) |
Now we need to import the Trusted Publishing Domain (TPD) for our RMS. A TPD contains the settings needed to use RMS features in your organization. For e.g. Users can apply RMS templates to email messages. To import TPD below cmdlet is used.
Import-RMSTrustedPublishingDomain -RMSOnline -name "RMS Online"
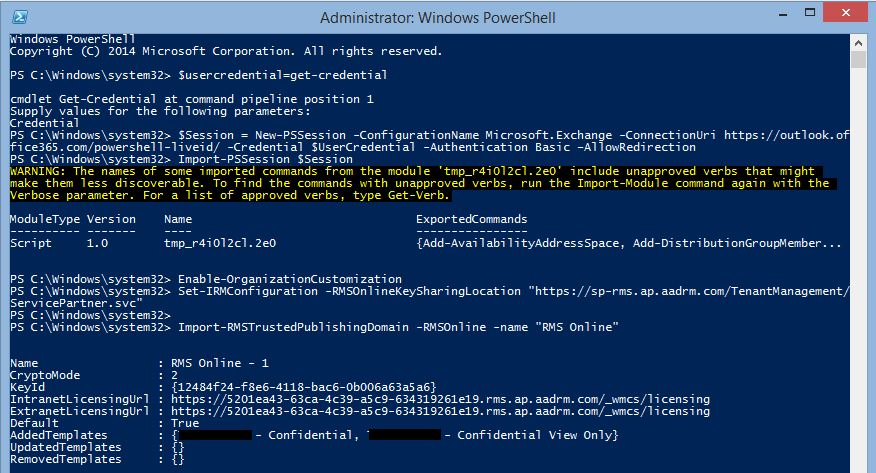
After importing TPD and before confirming the customization, we can make a test for the configuration with below cmdlet.
Test-IRMConfiguration -RMSOnline
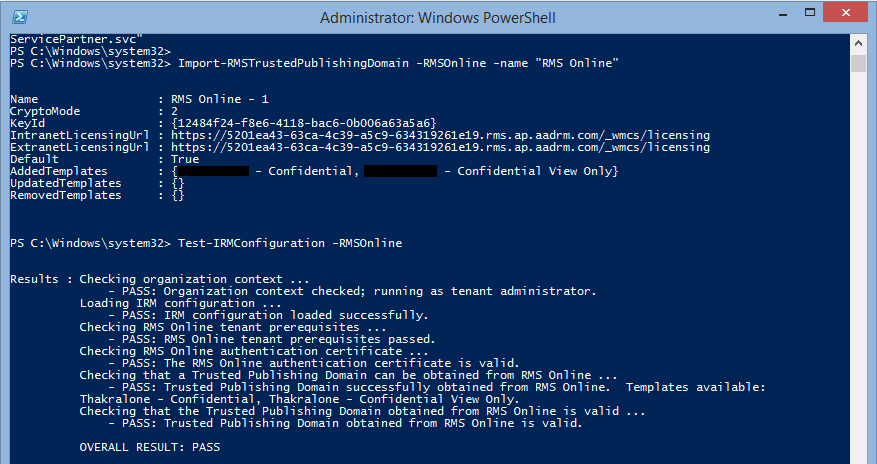
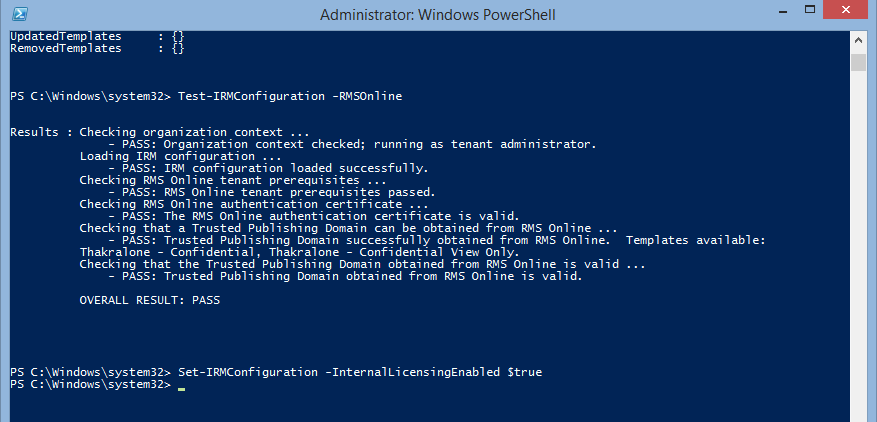
If the result of the IRM configuration test is found to be Pass, we can set the configuration with below cmdlet. And that’s all you have configured RMS for your Exchange online/ O365
Set-IRMConfiguration -InternalLicensingEnabled $true
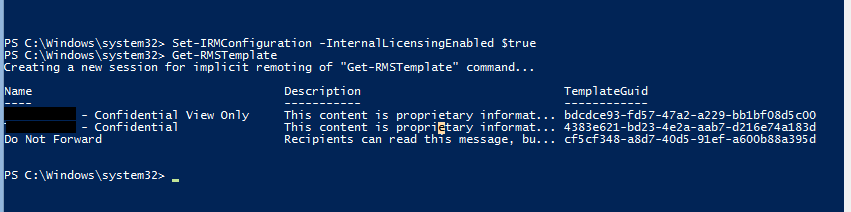
You can get the default templates of the RMS with below cmdlet
Get-RMSTemplate
Testing…
After the configuration of RMS on the Exchange Online/ O365, whenever user tries to send a sensitive email. They can select on more à Set Permissions à and required restriction for that email.
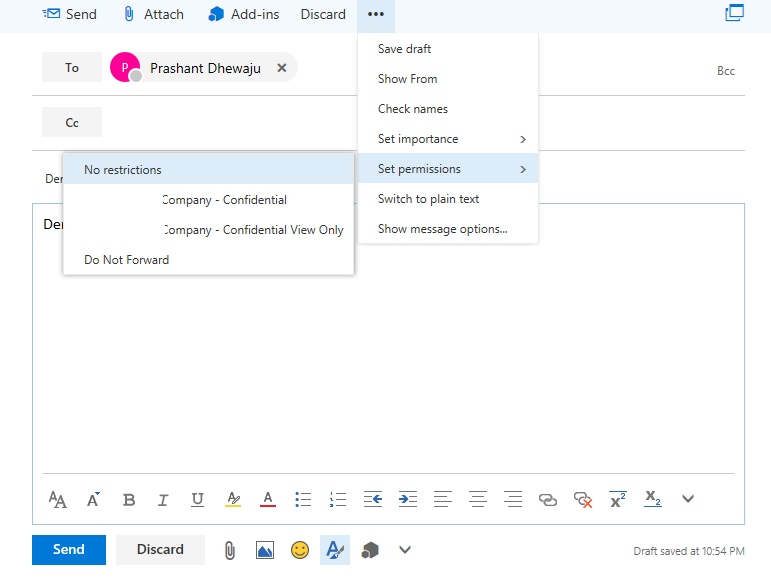
Once, the restriction on the email has been selected, there appear a notification with the restriction applied to that email.
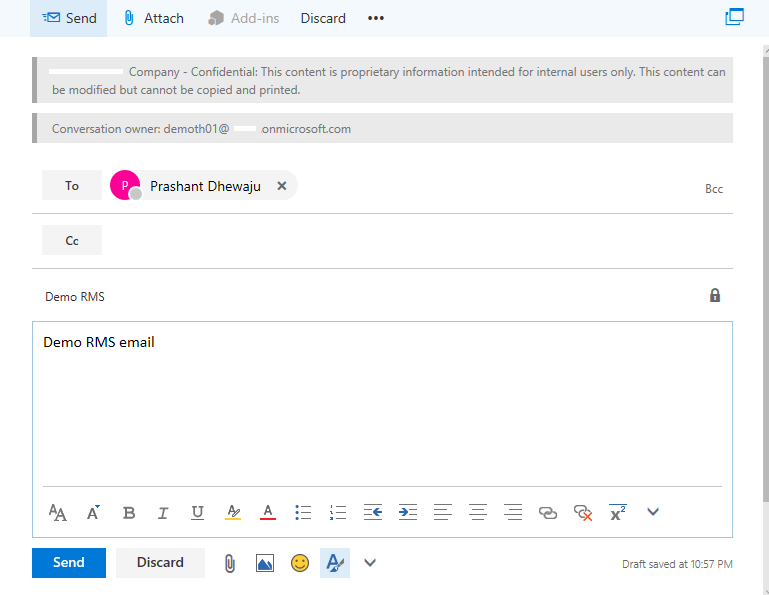
When the email is received from the recipient, he will get the notification on email with special restriction. As well notification on the email.
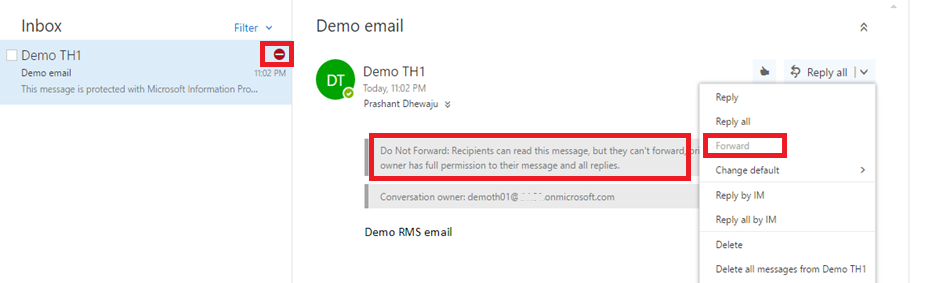
I hope this was easy configuration. If need any assistance on this regard, please leave comment. J
Related Posts

Changing Product key in Windows XP.

Schedule Task Manually…….how?

Customizing Message format and font on Office 365
About Author
pdhewjau
Prashant is a Principal Cybersecurity Specialist at Thakral One Nepal. His prior position as a Modern Work Security Specialist at Microsoft saw him providing invaluable guidance to major clients in Bangladesh, Brunei, Cambodia, and Myanmar, assisting them with their foundational security needs. Awarded the esteemed Microsoft Most Valuable Professional (MVP) accolade in 2017, Prashant is recognized globally among Microsoft peers. Since 2010, he has imparted his expertise as a Microsoft Certified Trainer (MCT), conducting specialized training across Nepal.