Immutable Hard matching on Azure AD
As a solution partner, I have seen lots of requests from my customers to synchronize their cloud identity to the on-premises. In most cases, they start with a small number of employees for which they don’t need to have servers and workloads in their on-premises. Cloud satisfies all their requirements and when they grow, they need to have some workloads on their premises with the SSO (single sign on). Now, the question is how to solve this requirement. For which we will be talking about Immutable Hard matching on Azure AD in this blog post.
As explained in my previously, what if we need to sync our Active Directory (AD) to the existing users in the cloud. Will it impact on the services or not and how can we do it easily.
So, let me start with my lab environment, on which I have a few users on the cloud, and I will be synchronizing that existing user from local AD to M365. On the below scenario, you can see I have a username ‘pdhewaju@mdm.pdhewaju.com.np’ which is cloud user.

Now the very first step is to have local AD and we need to install and configure ‘Azure AD connect’ in one of the servers connected to the internet. And as a recommended practice, we don’t synchronize all the domains or OU to the M365 (Azure AD) because it might sync unnecessary objects too instead, we synchronize only those domains and OU’s which is necessary. Below is the screenshot on how we can do it.
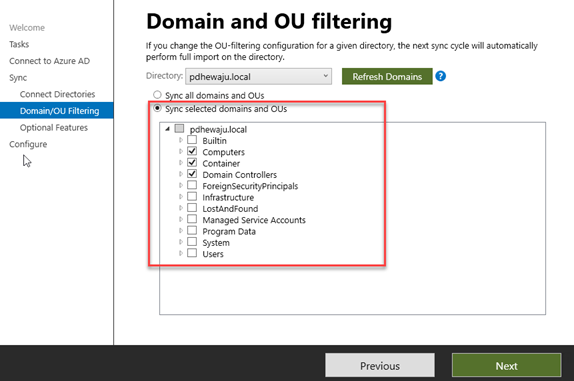
Because I hear I have already followed the best practices, I have synced only a few of the OU’s which is necessary for me to sync with Azure AD (M365). Now the critical part over here is you need to have exact username as of cloud user on your local AD. If you have mismatch username, it will create a new user instead of overwriting on existing user. So, make sure you have a correct username as on the cloud of that specific user.
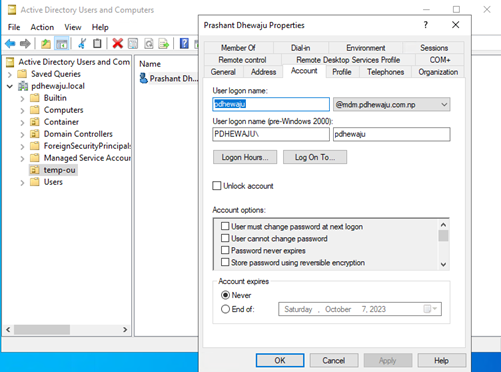
Once you have a user, now you need to pull the immutable for this user. Immutable are generated from ObjectGUID of each user and then hashed, hence it is unique for each user. To extract the ObjectGUID, you can use the cmdlet ad shown in the screenshot. (you need to perform this action on AD connect server)
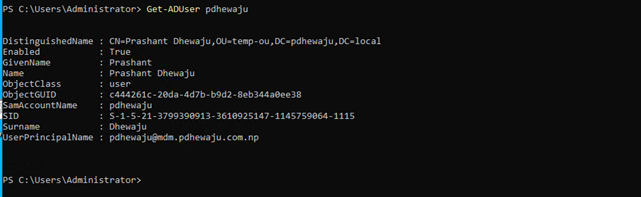
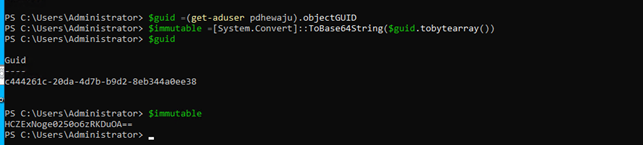
$guid =(get-aduser <identity>).objectGUID $immutable =[System.convert]:ToBase64String($guid.tobytearray())
Now you need to have “MSonline” PowerShell (PS) module installed in your machine to match the immutable. If you have any confusion on installation of MSonline PS module in your machine. You can follow below docs guidelines.
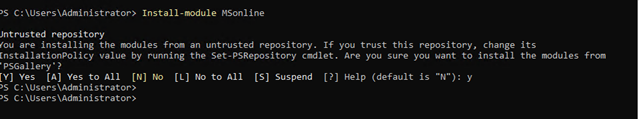
Once you have installed MSonline, now you can connect to MsolService and match immutable with cloud user using below cmdlet.
Set-MsolUser -UserPrincipalName <user principal name> -ImmutableID $immutable
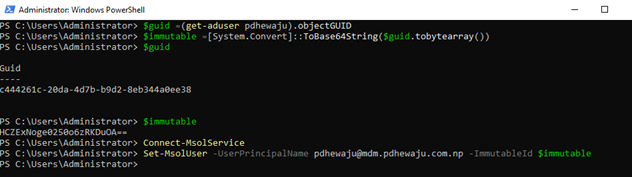
After setting immutable now you can resync Azure AD to bind local user with cloud user.
Start-ADSyncSyncCycle -PolicyType initial
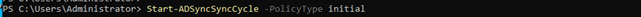
Once you have completed the synchronization, you will see the user status as on-premises.

Also, for details, you can visit this URL.
https://github.com/pdhewaju/M365/tree/main/Immutable%20Hardmatching
Related Posts

What new in Windows 8?
Microsoft Release wannacry/cryware Ransomware patch for Windows XP and Windows Server 2003

Configuring Virtual Directories on Exchange 2016.
About Author
pdhewjau
Prashant is a Principal Cybersecurity Specialist at Thakral One Nepal. His prior position as a Modern Work Security Specialist at Microsoft saw him providing invaluable guidance to major clients in Bangladesh, Brunei, Cambodia, and Myanmar, assisting them with their foundational security needs. Awarded the esteemed Microsoft Most Valuable Professional (MVP) accolade in 2017, Prashant is recognized globally among Microsoft peers. Since 2010, he has imparted his expertise as a Microsoft Certified Trainer (MCT), conducting specialized training across Nepal.