Disabling Basic Authentication on Exchange Online
Basic authentication provides a well basic level of security for your client application. Although this is not recommended due to vulnerabilities and exploits that can simply expose the user password. Some exploits like Password spraying attacks and Brute Force attack. It was on the roadmap of office 365 for Disabling Basic Authentication on Exchange online. So while disabling the Basic Authentication, we need to make sure email clients and apps must support modern authentication. Modern authentication for exchange online is supported by
- Outlook 2013 or later (note outlook 2013 requires a registry key change)
- Outlook 2016 for Mac or later
- Outlook for iOS and Android
- Mail for iOS 11.3.1 or later
Also here are three important caveats to this feature:
- There is a lack of telemetry for tenant admins allowing them to report on which users are using Basic Auth (and with which protocol) and once a block is enabled, whether such traffic was blocked. In other words, we can’t really tell you how well the block is working.
- A policy change can take up to 24 hours to take effect, unless the admin calls a cmdlet (such as Set-User) to ‘tickle’ each user. (Note that ‘tickling’ is a technical term, first used here). So the block might not kick in right away, and you might have to take some action if you want it to happen faster.
- If a user’s identity has not been replicated to Azure AD/Exchange Online, they will not be blocked and so any request received by Exchange Online will be routed to the authoritative Security Token Service (STS) where it is likely to fail. This same behavior also means that any authentication requests for unknown users in a tenant (such as might happen during a password spray attack) will also be forwarded to the authoritative STS for the domain.
- By disabling the Basic Authentication, you will not be able to get login in Exchange Online PowerShell Module.
Disabling Basic Authentication
To disable the basic authentication, we do have preview available on exchange online with the cmdlet New-AuthenticationPolicy. To disable the Basic Authentication, we need to create new authentication policy.
New-AuthenticationPolicy -Name "Disable Basic Auth"
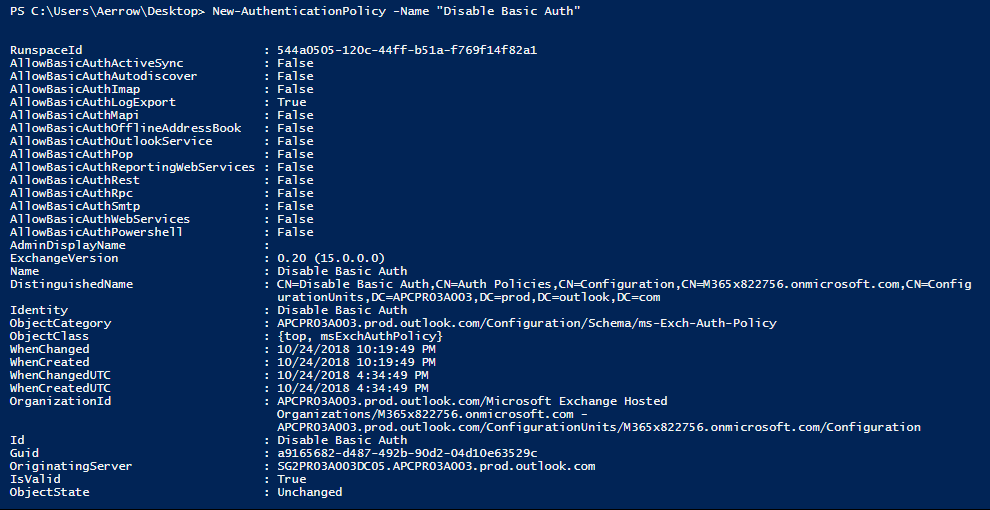
So over here you can see the AllowBasicAuth* has been false. i.e. not enabled.
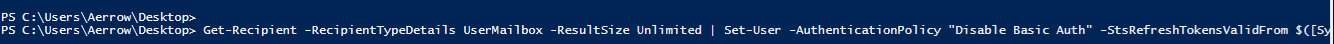
Now applying this policy to users
Get-Recipient -RecipientTypeDetails UserMailbox -ResultSize Unlimited | Set-User -AuthenticationPolicy "Disable Basic Auth" -StsRefreshTokensValidFrom $([System.DateTime]::UtcNow)
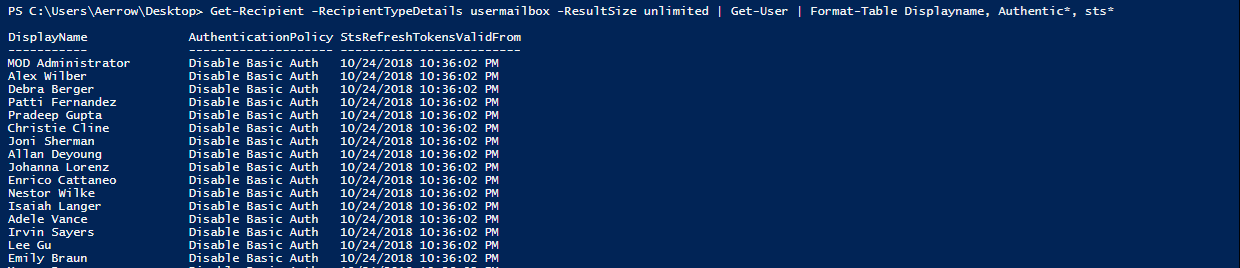
Get-Recipient -RecipientTypeDetails usermailbox -ResultSize unlimited | Get-User | Format-Table Displayname, Authentic*, sts*
Roll Back
If we do have some issues with the disabling the basic authentication, we can simply roll back with the below cmdlet.
Set-User -Identity "aerrow" -AuthenticationPolicy $Null

