Restrict Guest Access Permission in Azure Active Directory
Allowing Guest users to access the Azure Active Directory might be one of the compliance issues for the organization. Although, It’s great that the Guest users member of M365 Groups can access the resources like Plan, Sites, and Teams. When we talk about the Guest users, we always try to limit the access to these users. By default, Guest users do have Limited Access (i.e. Guest can se membership of all non-hidden groups) as of below:
| Permission level | Access level |
| Same as member users | Guests have the same access to Azure AD resources as member users |
| Limited access (default) | Guests can see membership of all non-hidden groups |
| Restricted access (new) | Guests can’t see membership of any groups |
So, there is a new feature on which we can Restrict Guest not to display membership of any groups. When guest access is restricted, guests can view only their own user profile. Permission to view other users isn’t allowed even if the guest is searching by User Principal Name or objectId. Restricted access also restricts guest users from seeing the membership of groups they’re in.
To configure this setting, you need to get login into your Azure Active Directory Admin Center.
Select Azure Active Directory ->External Identities.
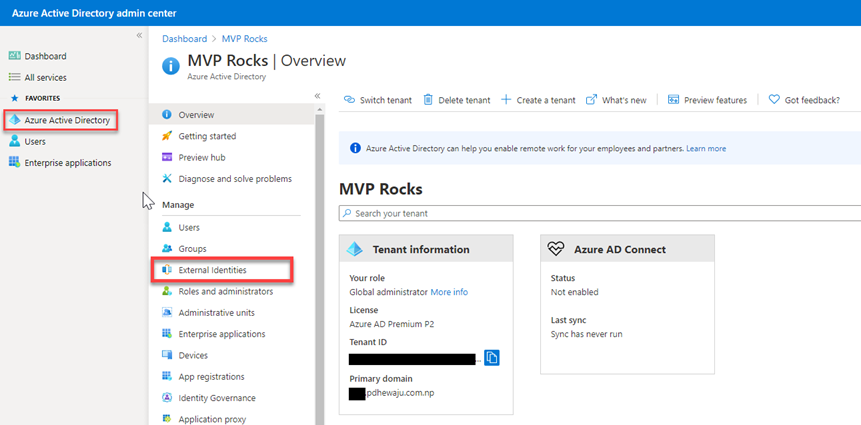
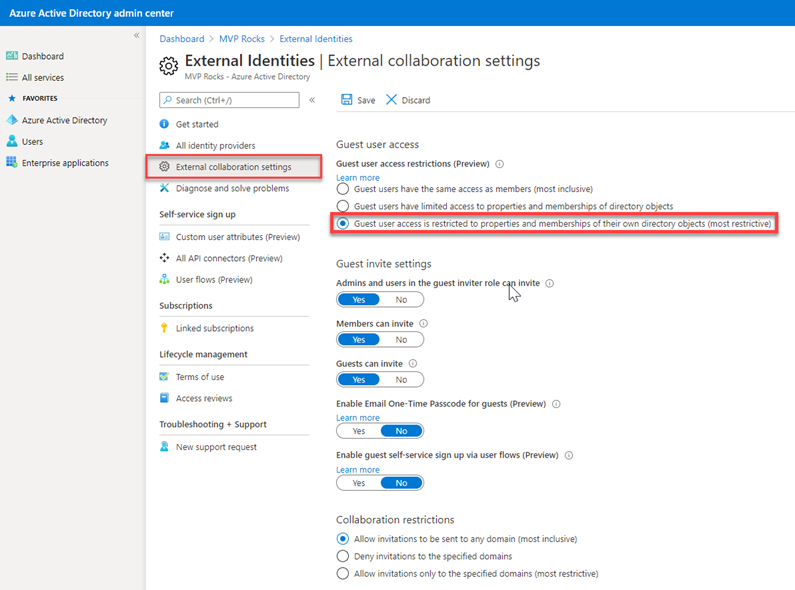
Select External Collaboration Settings and select ‘Guest User access is restricted to properties and memberships of their own directory objects (most restrictive)‘.
Similarly, we can configure this using Cmdlet too. To make changes, we can simply follow below cmdlet.
Connect-AzureAD Get-AzureADMSAuthorizationPolicy
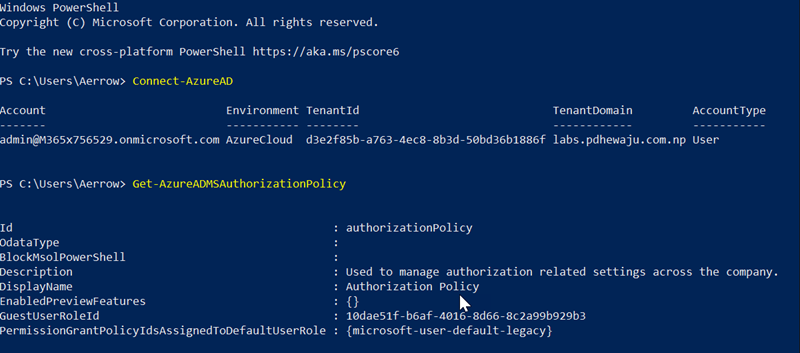
We can see that the GuestUserRoleID is configured as 10dae51f-b6af-4016-8d66-8c2a99b929b3 Which says to Limited Access.
The value of the GuestUserRoleId property contains the identifier (GUID) for the chosen template policy. The values of the identifier are:
- a0b1b346-4d3e-4e8b-98f8-753987be4970: Same access as Tenant members
- 10dae51f-b6af-4016-8d66-8c2a99b929b3: Limited access (default)
- 2af84b1e-32c8-42b7-82bc-daa82404023b: Most Restrictive
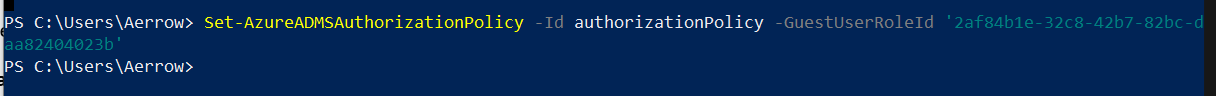
If we need to change it to restricted access, we need to use below cmdlet.
Set-AzureADMSAuthorizationPolicy -Id authorizationPolicy -GuestUserRoleId '2af84b1e-32c8-42b7-82bc-daa82404023b'
I hope this will help you to make your Azure AD more secure.
Related Posts

DLP Policy using Exchange Online PowerShell
![[FIXED] JUMPLIST disappear in Windows 7](/wp-content/themes/ribbon-lite/images/nothumb-related.png)
[FIXED] JUMPLIST disappear in Windows 7

Privacy Center Rogue Antivirus Copies Microsoft Privacy Portal
About Author
pdhewjau
Prashant is a Principal Cybersecurity Specialist at Thakral One Nepal. His prior position as a Modern Work Security Specialist at Microsoft saw him providing invaluable guidance to major clients in Bangladesh, Brunei, Cambodia, and Myanmar, assisting them with their foundational security needs. Awarded the esteemed Microsoft Most Valuable Professional (MVP) accolade in 2017, Prashant is recognized globally among Microsoft peers. Since 2010, he has imparted his expertise as a Microsoft Certified Trainer (MCT), conducting specialized training across Nepal.