Wannacry/cryware ransomware Outbreak
Since last Friday (May 12, 2017) there has been massive cyber-attack at Europe bring down a lot of computers from different organization including Schools and Hospitals. This has been major attack that none of has expected. Wannacry/cryware ransomware outbreak is having a major issue now.
What’s interesting about this ransomware is that WannaCry attackers are leveraging a Windows exploit harvested from the NSA called EternalBlue, which was dumped by the Shadow Brokers hacking group over a month ago.
Microsoft released a patch for the vulnerability in March (MS17-010), but many users and organizations who did not patch their systems are open to attacks.
The exploit has the capability to penetrate into machines running unpatched version of Windows XP through 2008 R2 by exploiting flaws in Microsoft Windows SMB Server. This is why WannaCry campaign is spreading at an astonishing pace.
Once a single computer in your organization is hit by the WannaCry ransomware, the worm looks for other vulnerable computers and infects them as well.
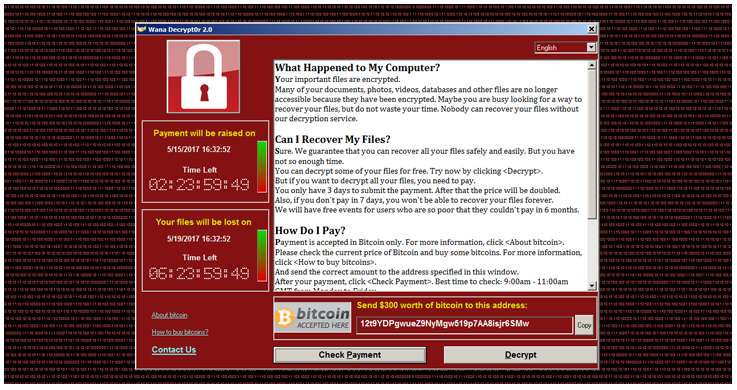
Indicators of compromise
SHA1 of samples analyzed:
- 51e4307093f8ca8854359c0ac882ddca427a813c
- e889544aff85ffaf8b0d0da705105dee7c97fe26
Files created:
- %SystemRoot%\mssecsvc.exe
- %SystemRoot%\tasksche.exe
- %SystemRoot%\qeriuwjhrf
- b.wnry
- c.wnry
- f.wnry
- r.wnry
- s.wnry
- t.wnry
- u.wnry
- taskdl.exe
- taskse.exe
- 00000000.eky
- 00000000.res
- 00000000.pky
- @WanaDecryptor@.exe
- @Please_Read_Me@.txt
- m.vbs
- @WanaDecryptor@.exe.lnk
- @WanaDecryptor@.bmp
- 274901494632976.bat
- taskdl.exe
- Taskse.exe
- Files with “.wnry” extension
- Files with “.WNCRY” extension
Registry keys created:
- HKLM\SOFTWARE\WanaCrypt0r\wd
Karthik Selvaraj, Elia Florio, Andrea Lelli, and Tanmay Ganacharya
Microsoft Malware Protection Center
How to be Secure?
- Immediately apply the Microsoft Patch MS17-010 from below link to your respective machine
https://technet.microsoft.com/en-us/library/security/ms17-010.aspx
For XP machine Patch Visit this blog
- Do not open any suspicious email with attachment or click on any link that has been provided on the email. Even though it seems like PDF or any office files.
- Make a backup of your files to the different location than your PC.
- This worm targets out of date systems, so keep updating
Sources:
http://www.bbc.com/news/technology-39901382?SThisFB
http://thehackernews.com/2017/05/wannacry-ransomware-unlock.html?m=1